Global Cyber Weapon Market Set for Rapid Growth, To Reach Around USD 28.5 Bn by 2033

Page Contents
Market Overview
Published Via 11Press : Cyber weapons are the tools, techniques, and capabilities used to conduct cyber operations against individuals, organizations, or governments, such as espionage, sabotage, or warfare. These weapons include software , malware, viruses, Trojans, and other forms of malicious code.
Cyber weapons Market is capable of compromising computer systems, stealing sensitive data, disrupting vital infrastructure, and even causing physical harm to equipment. They can also be employed for psychological operations and propaganda, such as the dissemination of deceptive information and the manipulation of public opinion.
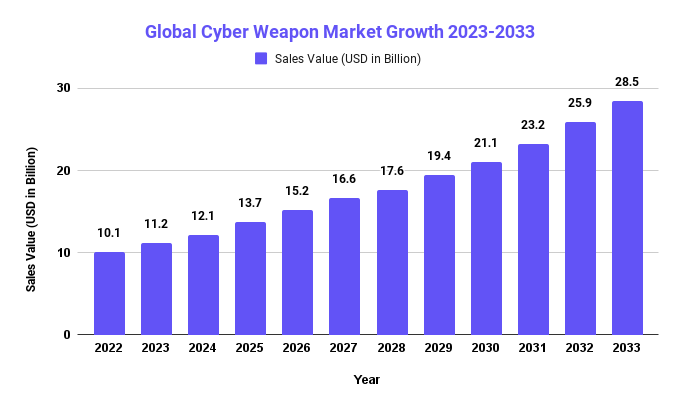
The Cyber Weapon Market size is expected to reach USD 28.5 Bn by 2033, up from its current value of USD 10.1 Bn in 2022, growing at an annual compound growth rate (CAGR) of 10.1% from 2023-2033.
Cyber weapons are typically developed and employed by nation-states, intelligence agencies, and military organizations. However, non-state actors such as terrorist groups and criminal organizations are also capable of developing and deploying cyber weapons.
Stuxnet, a computer malware that targeted Iran's nuclear program in 2010, and the WannaCry ransomware attack that affected thousands of computers worldwide in 2017 are well-known examples of cyber weapons. Other examples include the Flame malware, the Shadow Brokers disclosure of NSA hacking tools, and the NotPetya malware, which caused billions of dollars in damages to businesses around the world in 2017.
Cyber weapons are a growing concern for governments, businesses, and individuals equally, as their proliferation could have grave consequences for global security and stability. Consequently, there are ongoing discussions and debates regarding the development, deployment, and regulation of cyber weapons.
Key Takeaways
- Cyber weapons are tools, techniques and capabilities used in cyber operations – such as espionage, sabotage and warfare against individuals, organizations or governments – such as spying.
- Cyber weapons encompass software, malware, viruses, Trojans and any other form of malicious code that could threaten our digital security.
- Cyber weapons have the ability to disrupt computer systems, steal sensitive data, disrupt critical infrastructure systems and cause physical harm to equipment.
- Cyber weapons are typically created and deployed by nation-states, intelligence agencies, and military organizations; however, terrorist groups or criminal organizations are capable of developing and employing cyber weapons as well.
- Stuxnet, WannaCry ransomware, Flame malware, the Shadow Brokers' release of NSA hacking tools and NotPetya are well-known cyber weapons.
- Cyber weapons have become a growing source of concern for governments, businesses, and individuals alike, as these capabilities and tools may pose grave threats to global security and stability.
- Cyber weapons remain the subject of ongoing discussions and debate, as efforts are made to develop international norms and agreements to address them.
Regional Snapshot
- The United States is a leader in developing and employing cyber weapons within North America, spearheaded by its National Security Agency (NSA) and U.S. Cyber Command respectively. Their respective offensive cyber capabilities are responsible for developing Stuxnet and 2016 election interference attacks; both can be found here.
- European nations have taken an active approach in building defensive cyber capabilities, while Russia and China are well known to have launched cyber attacks against European nations. As part of a multilateral effort to strengthen cybersecurity across member states, the European Cybersecurity Agency was recently created in Brussels.
- China is widely considered an active participant in cyber warfare and has been accused of conducting cyber attacks against multiple nations, including the US. North Korea has also been charged with using cyber attacks as a method for raising funds and collecting intelligence. Japan recently established a cyber defense unit to further improve their cyber capabilities.
- Israel is well known for its cyber capabilities and has been involved in high-profile cyber attacks, such as Stuxnet, in the Middle East region. Iran is also suspected of initiating cyber attacks against Saudi Arabia and the US.
- Africa's cyber capabilities are still evolving, although some nations are investing in cyber defense systems and devising national cyber security strategies. South Africa leads the continent in terms of developing cyber capabilities.
Any inquiry, Speak to our expert at: https://marketresearch.biz/report/cyber-weapon-market/#inquiry
Drivers
- Governments and military organizations may develop and deploy cyber weapons to defend their nations and interests from potential cyber attacks by other nations or non-state actors.
- Cyber weapons can be used to acquire trade secrets, intellectual property, and other sensitive information from foreign governments and businesses. This data can be utilized to obtain a competitive edge in the global marketplace.
- Cyber weapons can also be used for political espionage to amass information on political opponents and manipulate public opinion. This is frequently accomplished through the dissemination of false information or propaganda via social media and other online platforms.
- Cyber weapons can be used to disrupt vital infrastructure, including electrical grids, transportation systems, and communication networks. This can result in extensive disorder and economic harm.
- Criminal organizations can utilize cyber weapons to steal financial information, extort money from individuals and businesses, and engage in other unlawful activities.
- Terrorist organizations can use cyber weapons to disseminate propaganda, recruit new members, and disrupt vital infrastructure.
Restraints
- The United Nations Charter and international law offer guidelines for using force and weapons. Some experts argue that existing international laws pertain to cyber weapons; any usage must comply with such laws.
- Emerging norms and taboos exist concerning the use of cyber weapons against civilian targets. Concerns regarding potential consequences from attacks as well as difficulty controlling malware dissemination motivate these norms and taboos.
- Technical Restrictions: Developing effective cyber weapons requires both technical expertise and resources, but some nations or organizations may lack either financial or technical means to develop and deploy sophisticated cyberweapons.
- Cyber attacks, unlike traditional weapons, can often be difficult to attribute to specific individuals or nations, making it more challenging for nations to respond with military force due to lack of evidence that points towards the perpetrator.
- Misuse of cyber weapons may have unintended repercussions, including spreading malware to unintended targets or prompting nations or organizations targeted to respond with counter measures – leading to an unpredictable cycle of escalated and counteracted violence.
- There are various factors which could restrict the creation and use of cyber weapons. Their ever-evolving technology and lack of specific international guidelines makes it hard to anticipate their effectiveness as future restrictions.
Opportunities
- Increased Interconnectivity: As our world grows more interconnected, cyber attacks become more likely. For instance, IoT devices present new vulnerabilities which cybercriminals could exploit. Government and military organizations therefore have the chance to develop and deploy cyber weapons to protect national interests.
- Economic Interests: Many nations consider cybercapabilities essential to their economic wellbeing. Cyber attacks can be used to gain competitive edge on the global cyber weapon market and obtain intellectual property or disrupt competitors – this enables governments and corporations to employ cyber weapons to meet their economic objectives.
- Cyberattacks can be employed to gather intelligence on political opponents and manipulate public opinion for political gain, giving governments and political organizations an edge in elections or other campaigns by employing cyber weapons as part of their arsenal.
- Artificial Intelligence and Quantum Computation innovations provide governments and military organizations with opportunities for developing more advanced cyber weapons to maintain strategic advantage against rival organizations. This allows governments and military forces to maintain strategic advantage and stay ahead of their adversaries.
- Cybercriminals are constantly searching for ways to exploit vulnerabilities and steal valuable data, giving criminal organizations the ability to develop and deploy cyber weapons that help achieve their goals.
Request Sample Copy of Cyber Weapon Market Report at: https://marketresearch.biz/report/cyber-weapon-market/request-sample/
Challenges
- Obstacles to Success: In order to craft effective cyber weapons, hackers require extensive technical proficiency and resources. Attackers must be capable of identifying software and network vulnerabilities, creating exploits for those vulnerabilities, and designing malware which evades security measures.
- Attribution Difficulties: Attributing cyber attacks can be challenging. Attackers use techniques like spoofing and relaying through multiple intermediaries to conceal their identities and locations, making it hard for governments to respond with force due to lack of evidence that pinpoints a culprit.
- Legal Obstacles: With no international guidelines regulating cyber weapons use, it can be challenging to determine what constitutes legal use and what does not. Existing laws may not address all the unique challenges posed by cyber warfare.
- cyber weapons may produce unintended results, including the dissemination of malware to targets not intended by their use, or targeted nations retaliating in kind – creating an unpredictable cycle of escalation and retaliation.
- Strategic Barriers: Cyber warfare is an ever-evolving field, so governments and military organizations must invest continually in R&D to maintain their strategic advantage and remain ahead of adversaries at all times.
Market Segmentation
Type
- Defensive
- Offensive
Application
- National Defense System
- Air Traffic
- Hospital
- Automated Transportation System
- Industrial System
- Communication network
- Smart power grid
- Others
Key Players
- Boeing Company.
- Lockheed Martin Corporation.
- Cisco Systems
- McAfee Inc.
- General Dynamics Corporation
- BAE Systems plc.
- Symantec Corporation
- Northrop Grumman Corporation
- Raytheon Company.
- General Dynamics Corporation
Report Scope
| Report Attribute | Details |
| Market size value in 2022 | USD 10.1 Bn |
| Revenue forecast by 2033 | USD 28.5 Bn |
| Growth Rate | CAGR Of 10.1% |
| Regions Covered | North America, Europe, Asia Pacific, Latin America, and Middle East & Africa, and Rest of the World |
| Historical Years | 2017-2022 |
| Base Year | 2022 |
| Estimated Year | 2023 |
| Short-Term Projection Year | 2028 |
| Long-Term Projected Year | 2033 |
Recent Developments
SolarWinds hack (2020): In late 2020, a sophisticated cyber attack that compromised multiple U.S. government agencies and private companies was discovered. Believed to have been conducted by Russian hackers, it involved injecting malware into widely-used software from SolarWinds company.
Colonial Pipeline, a major U.S. pipeline company, was recently hit with a ransomware attack which temporarily disrupted fuel supplies on the East Coast. DarkSide, believed to be based in Russia, has been identified as being responsible for this heinous act.
Stuxnet Attack on Iranian Nuclear Program (2010): In 2010, it was discovered that Stuxnet, a sophisticated malware program, had been employed to disrupt centrifuges at an Iranian nuclear facility and widely believed by experts to have been carried out by both the United States and Israel.
NotPetya Attack (2017): In 2017 a devastating cyberattack targeted businesses and organizations around the world, including Ukraine where it caused severe disruption. Although initially believed to be caused by ransomware attacks, now it is believed to have been orchestrated by state-sponsored Russian hackers.
Shadow Brokers Leaks (2016): Beginning in 2016, an anonymous group known as Shadow Brokers started releasing classified information regarding US government's cyber capabilities, such as exploits and tools utilized by National Security Agency. Russian hackers are believed to be behind these disclosures.
These are only a few recent advancements in cyber weapons and attacks. Their use continues to evolve, so more advances could likely arise in the near future.
Key Questions
What exactly are cyber weapons?
Cyber weapons are the instruments and methods used to conduct cyber attacks. They can include malware, viruses, and other forms of malicious code, in addition to exploits and other techniques for exploiting software and network vulnerabilities.
Who employs cyberweapons?
A variety of actors, including nation-states, criminal organizations , and activists, can employ cyber weapons. Governments and military organizations are typically the primary consumers of cyber weapons, as they possess the resources and expertise necessary to develop and deploy these tools.
What are the dangers associated with cyber weapons?
The use of cyber weapons may result in unintended outcomes, such as the dissemination of malware to unintended targets or the retaliation of targeted nations or organizations. As nations respond to cyber assaults with military force, there is also the possibility that cyber attacks will escalate into more traditional forms of warfare.
How can we defend ourselves from cyberweapons?
A multilayered approach is required to defend against cyber weapons, including technical measures such as firewalls and antivirus software, as well as risk management policies and procedures. In addition, organizations must be vigilant in monitoring their networks for intrusion indicators and responding swiftly to potential attacks.
What are the prospects for cyber weapons?
As technology advances and the threat landscape shifts, the use of cyber weapons is likely to continue to evolve. Governments and military organizations are likely to continue investing in R&D to maintain their strategic advantage, whereas criminal organizations and activists are likely to increase the sophistication of their cyberattacks.
Contact us
Contact Person: Mr. Lawrence John
Marketresearch.Biz (Powered By Prudour Pvt. Ltd.)
Tel: +1 (347) 796-4335
Send Email: [email protected]
Content has been published via 11press. for more details please contact at [email protected]
The team behind market.us, marketresearch.biz, market.biz and more. Our purpose is to keep our customers ahead of the game with regard to the markets. They may fluctuate up or down, but we will help you to stay ahead of the curve in these market fluctuations. Our consistent growth and ability to deliver in-depth analyses and market insight has engaged genuine market players. They have faith in us to offer the data and information they require to make balanced and decisive marketing decisions.