70+ Notable Ransomware Statistics And Trends 2023

Page Contents
- Vital Ransomware Statistics
- Ransomware attacks Statistics by country between 2022 to 2023
- Ransomware Statistics by cyberattacks by types in 2022
- Most Recent Ransomware Statistics
- Ransomware Statistics And Trends By Industry
- Ransomware Cryptocurrency Statistics
- Mobile Ransomware Trends
- Expenses Of Ransomware Cyber Attacks
- Ransomware Projection Statistics
- Various Evolving Ransomware Variants
- Methods To Prevent Ransomware Attacks
- Reducing The Effect of Ransomware Attack
- Conclusion
Ransomware Statistics: Ransomware is a type of malicious software that breaks into your computer or network, encrypts files, and restricts access to vital data until a ransom is paid. The first incident of ransomware software attack was reported in 1989 when floppy discs used to be an advanced tool and the cost of the ransom was hardly $189. Attacks carried out by ransomware have been increasing since then and it continues to be a troubling factor in the industry of cyber security. Such attacks affect a wide range of industries from financial institutions to higher education. Due to an increase in remote work approaches, the rate of ransomware attacks has shot up by 148 percent. Here we will discuss top ransomware statistics that will help consumers avoid such attacks in the future.
Vital Ransomware Statistics
- Worldwide ransomware attacks totaled 236.1 million in the first half of 2022.
- Overall, the number of ransomware attacks decreased rapidly between the second and fourth quarters of 2021, going from nearly 189 million cases to 133 million.
- The rate of malicious emails shot up by 600 percent during the COVID-19 pandemic in 2021.
- There were around 305 million malware attacks in 2020 worldwide.
- As of Q4 of 2022, there were 154.93 million ransomware attacks around the world.
- Furthermore, exploited vulnerability is the most common cause of ransomware attacks in 2023.
- In Q2 of 2023, the global amount of ransom payments amounted to $740,144.
- After ransom payments, 2022 data suggested that only 52% of the companies regained their access to data.
- In 2023, the average budget for companies around the world in terms of cybersecurity increased by 5.3%.
Ransomware attacks Statistics by country between 2022 to 2023
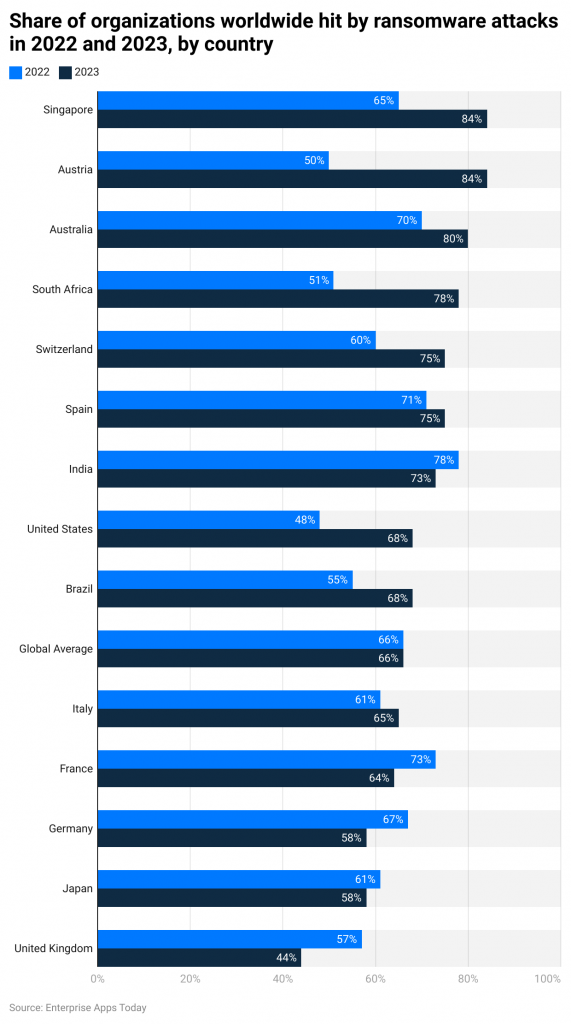
(Source: Statista)
- In 2022 and 2023, Singapore, Austria, and Australia were the top three countries with the highest number of organizations experiencing ransomware attacks. Comparatively, the number has even increased in 2023. On average, each listed country has more than a 50% rate of ransom attacks.
Ransomware Statistics by cyberattacks by types in 2022
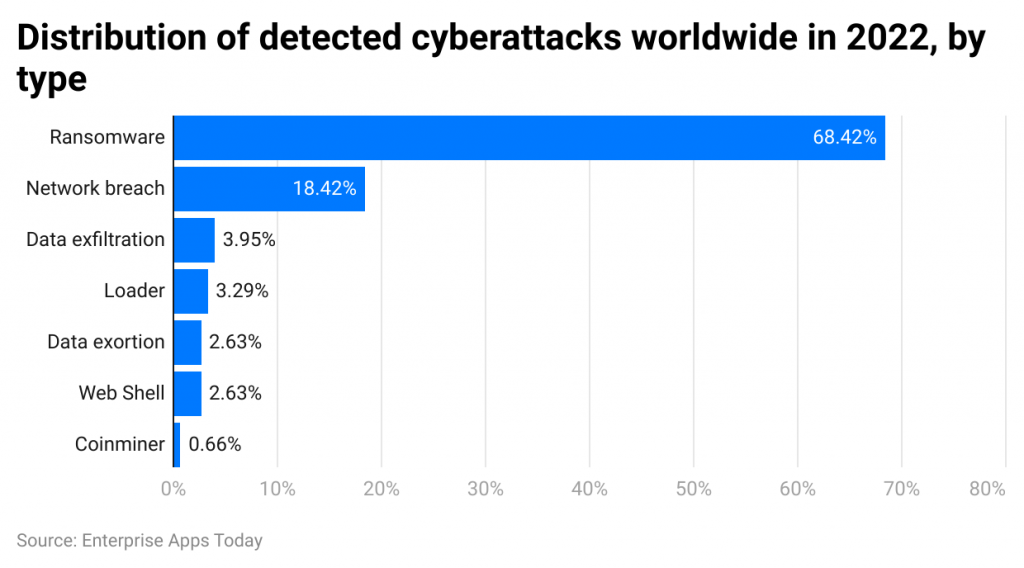
(Source: Statista)
- In 2022, Ransomware attack was the most common type of attack as it detected 68.42% of total cyberattacks in the world. The least reported was Coinminer resulting in 0.66%. Other two types of popular cyber attacks were Network Breaches (18.42%), and Data exfiltration (3.95%).
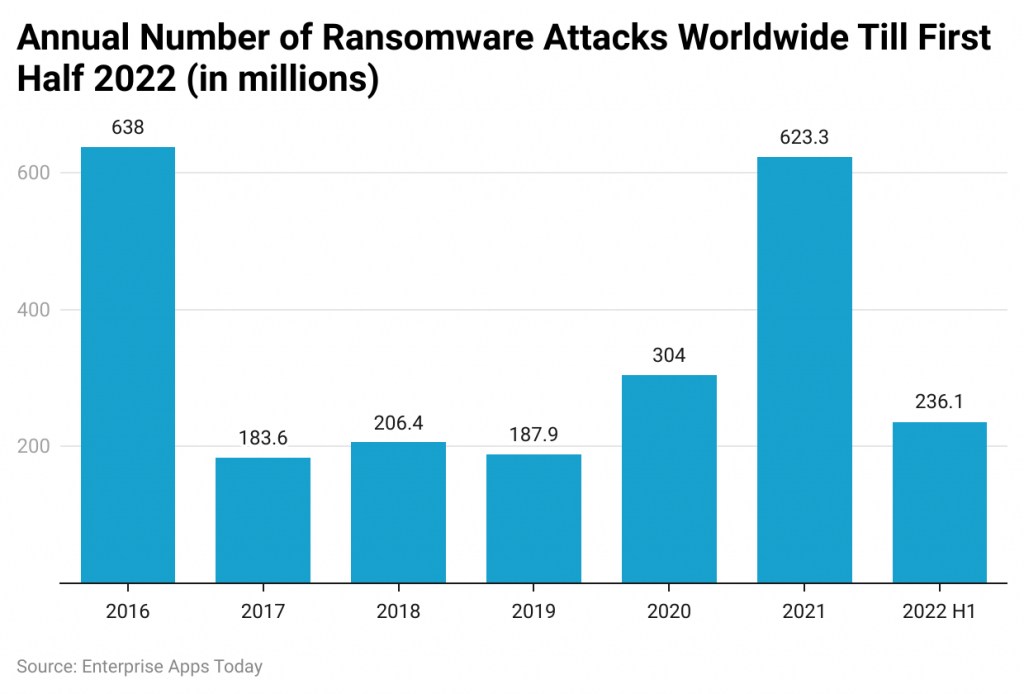
(Source: Statista)
- As per a survey, nearly 37 percent of organizations have been affected by ransomware attacks in 2021.
- Around 54 percent of firms in the US reported ransomware attacks in 2020.
- A company faces an average downtime of 22 days after ransomware hits.
- As per a study, ransomware is considered the top malware threat.
- In 2020, 54 percent of malicious cyber attacks took play due to users clicking on a malicious link in an email or downloading a virus-infected document.
- The cost of recuperating from a ransomware attack can shoot up to $1 million.
- The cost of recuperating from a ransomware attack was predicted to reach a new high of $20 billion in 2021.
- An insurance firm has paid a hefty ransomware payout of $40 million in 2021 that has set a world record.
- In 2021, 96 percent of 1086 organizations have been able to recover their encrypted data.
- As per ransomware statistics 2020, at least one in 6000 emails contained malicious URLs including ransomware attacks.
- The expected expenses linked to ransomware hitting a venture are $133000.
- Ransomware statistics in 2020 show that WannaCry led to nearly 50 percent of reported malware attacks in the US.
- Email phishing campaigns, Software vulnerabilities, and RDP vulnerabilities are the most common ways that hackers use to carry out ransom attacks.
Most Recent Ransomware Statistics
#1. Giant hardware vendor Acer reported a ransomware hit in 2021.
REvil ransomware group carried out this ransomware attack on the company in March 2021.
#2. During the same time, cyber insurance carrier CNA Financial as well admitted to being a victim of a ransomware attack.
This ransomware hit had been carried out by a ransomware group known as Phoenix. The insurance company has paid $40 million in ransom.
#3. Nearly 59 percent of firms allow their staff to access company apps on non-verified personal devices.
As per the ransomware statistics in 2021, more than half of companies let their staff members use their official apps on their personal devices. It can lead to bigger security threats.
#4. Most companies experience another cyber attack soon after paying out the ransom amount.
As per a survey done on 1263 firms, around 80 percent of firms have been the victim of another cyber attack soon after paying the first ransom amount. Around 46 percent of companies have been able to get their data back but most of the data has been corrupted.
#5. 60 percent of surveyed firms have admitted to having a revenue loss due to such cyber attacks.
Around 53 percent of firms have said that they have been dented due to such attacks. 29 percent of firms have said that they were compelled to remove positions after ransomware hit.
#6. 42 percent of surveyed firms said that cyber insurance policies covered only a small portion of the damages.
Many companies said that cyber insurance policies did very little to cover up the damages after ransomware hit.
#7. Colonial Pipeline reported having a ransomware hit in May 2021.
This ransomware attack impacted the flow of oil across the eastern US.
#8. Meat processing firm JBS USA as well has been hit by a ransomware attack in June 2021.
It reduced the firm's capacity to package meat products. As per ransomware statistics, the company gave away $11 million in ransom to the REvil ransomware group.
#9. Remote management software vendor Kaseya suffered a supply chain ransomware hit in July 2021.
This ransomware attack was carried out by the REvil ransomware group.
#10. In October 2021, Sinclair Broadcast Group as well became the victim of a ransomware cyber attack.
This attack affected the broadcast operations of the company.
#11. The cost of ransomware attacks was projected to touch $20 billion by the end of 2021.
In 2019, the predicted cost of ransomware hit $11.5 billion. As per the latest ransomware statistics, it will continue to grow in the future as well.
#12. More than 7000 people are affected by ransomware attacks per day.
As per ransomware statistics, a firm across the globe becomes the target of a ransomware attack every 11 seconds.
#13. 67 percent of ransomware hits are carried out by spam and phishing emails.
The latest ransomware statistics show that two-thirds of all ransomware attacks are carried out via spam and phishing emails. Around 36 percent of such attacks take place due to a lack of cyber training and 30 percent of remaining cyber attacks happen due to bad control access and weak passwords.
#14. Around 85 percent of such ransomware attacks target Windows users.
Nearly 85 percent of such attacks take place on Windows operating systems. Only 7 percent of such attacks target MacOS users. Whereas 5 percent of these cyber attacks target Android users.
#15. 56 percent of ransomware victims give away the ransom payout to cybercriminals.
Over half of the victims make ransom payments to ransomware criminals while 17 percent of them are not able to recover their data.
#16. WannaCry is considered the biggest ransomware attack in history.
The WannaCry ransomware attack took place in May 2017 and affected nearly 250000 systems across 150 nations and created a panic situation for four days around the world. It is considered the worst cyber attack in history.
#17. Nearly 36 percent of cyber hits aim to damage the business.
Although the ransom payout is the main goal of a cyber attack, the value of the business disruption resulting from the attack usually prevails over the ransom amount.
#18. 15.4 percent of ransomware attacks are targeted at government organizations.
Around 13.9 percent of such attacks are targeted manufacturing services and 13.2 percent of cyber hits target construction services.
#19. Around 50 to 70 percent of malware victims in the US are small corporations.
50 to 70 percent of all cyber attacks in the US hit small to medium-sized firms.
#20. A company faces an average downtime of 22 days after a ransomware hit.
As per the latest ransomware statistics, the total downtime triggered by ransomware cyber hits has shot up over the years.
#21. The cost of cybercrime is expected to be $5.2 trillion in 2023.
In the absence of sufficient cyber security measures, companies are expected to suffer major financial losses.
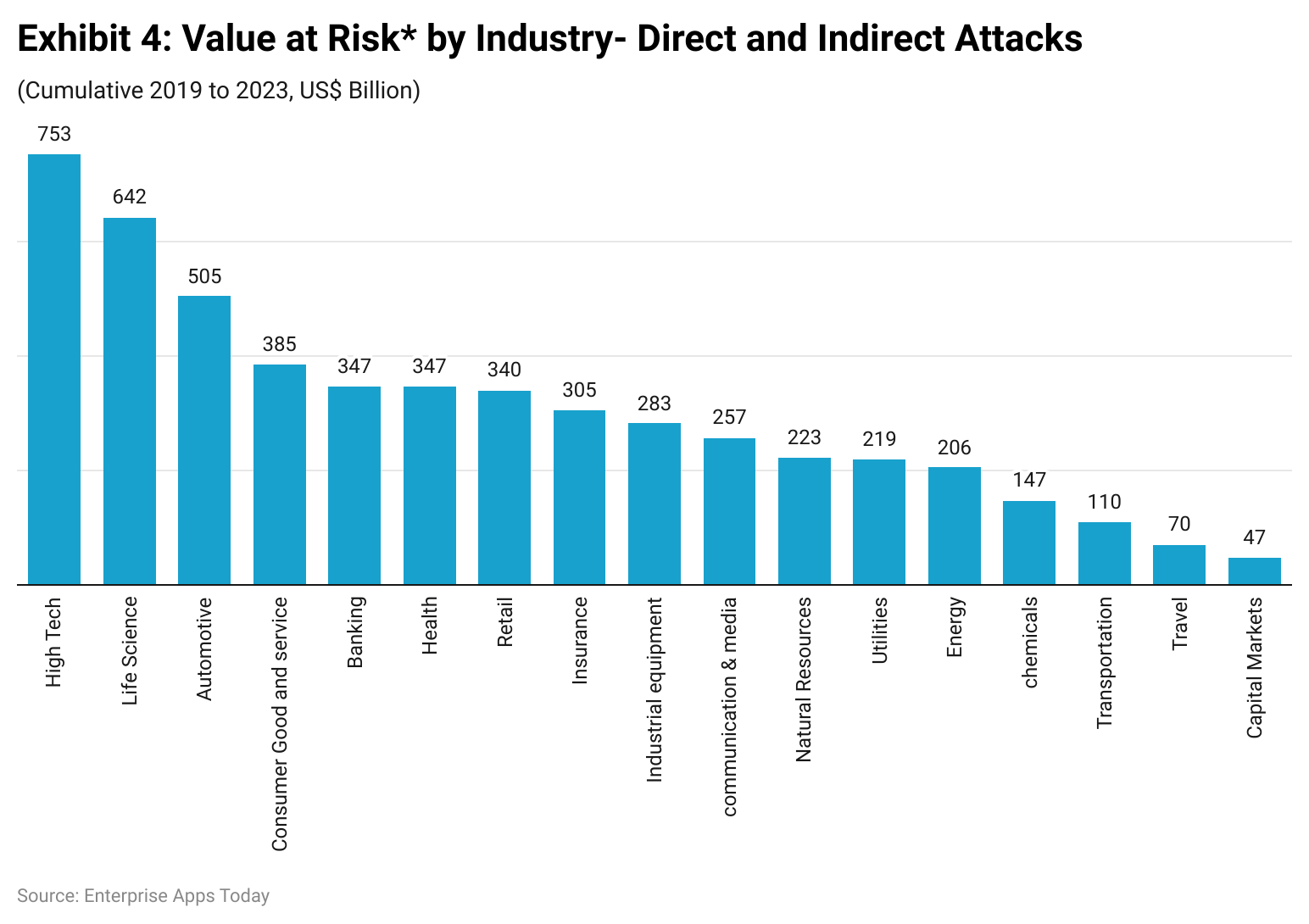
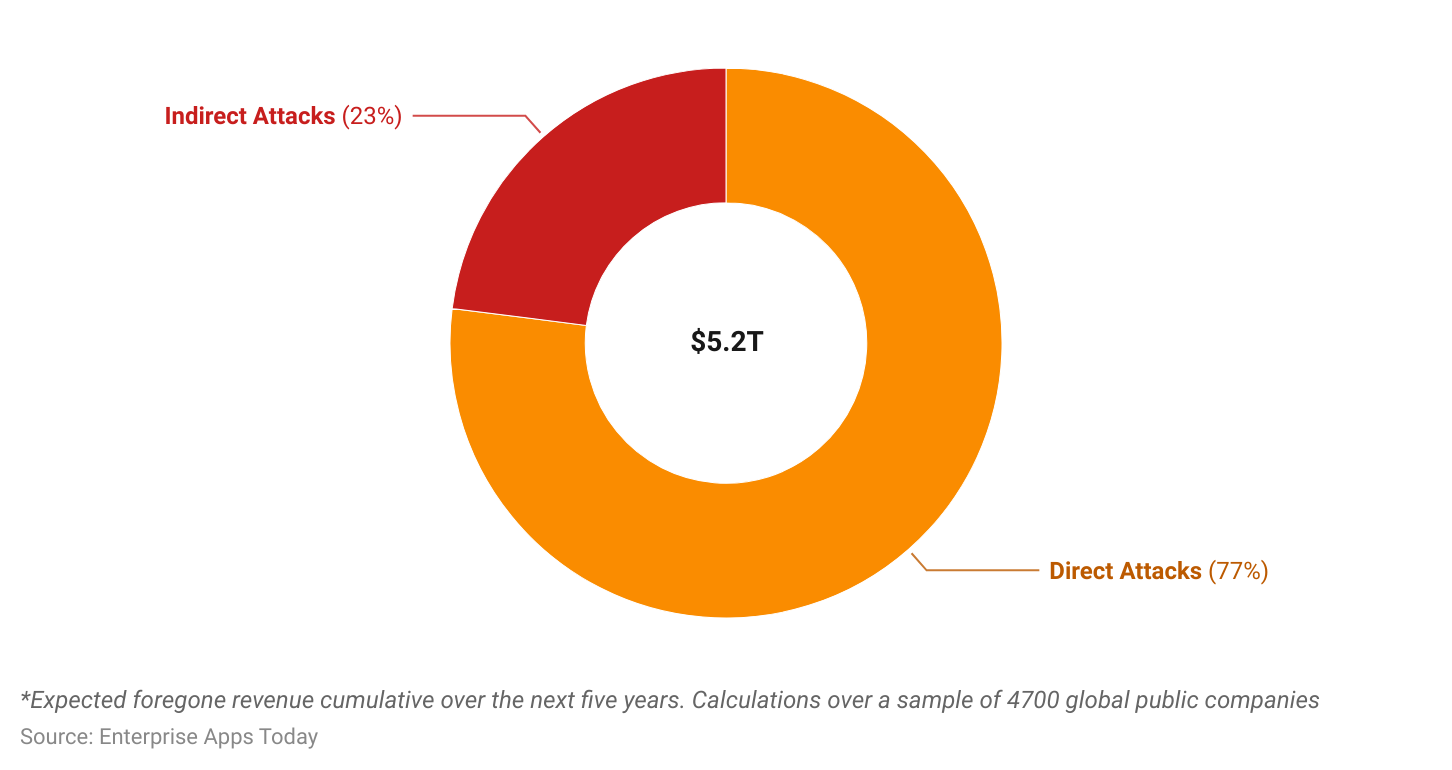
(Source: Accenture Research)
#22. High-tech firms are at the highest risk of cyber attacks in upcoming years.
Automobile and life science industries as well are at a higher risk of malware attacks in the future.
#23. The shipping industry might be the next victim of such cyber attacks.
As per the experts, the shipping and distribution industry might be the potential target for ransomware attacks in 2022.
#24. The number of ransomware attacks has shot up by 400 percent since the start of the COVID-19 pandemic.
The cost of a ransomware attack as well is much higher than ever.
#25. The demand for ‘ransomware as a service is predicted to shoot up in the future.
For amateur cyber criminals, ‘ransomware as a service (RaaS) is the best way to begin their illegal activities.
Ransomware Statistics And Trends By Industry
#26. Ransomware stats in 2020 show that healthcare firms spend a small sum of their budget on cyber security measures.
Healthcare firms only spend 6 percent of their budget on cybersecurity measures. While more than 2100 data breaches have been reported in this sector since 2009.
#27. In 2020, ransomware hits accounted for nearly half of all healthcare data violations.
Around 560 healthcare facilities were impacted by such cyber attacks in 80 different incidents.
#28. Cyber attacks on the healthcare industry cost more than any other trade.
It costs around $408 per compromised data in healthcare. Ransomware hits against healthcare facilities in the US led to a huge loss of more than $157 million since 2016.

(Source: Comparitech)
#29. The healthcare sector saw a 51 percent increase in the total volume of compromised data from 2019 to 2021.
In the first half of 2021, there had been nearly 2084 ransomware complaints.
#30. Ransomware attacks against universities shot up by 100 percent from 2019 to 2020.
As per the ransomware statistics in 2021, 66 percent of universities do not have basic email security configurations.
#31. The average price of a ransomware hit against the higher education sector is $447000.
Malware attacks against K-12 schools shot up to 18 percent in 2020.
#32. Around 1681 higher education institutes have been impacted by 84 ransomware cyber attacks since 2020.
Nearly 38 percent of universities that have been surveyed in the Cybersecurity in Higher Education report have been using unsecured or open database ports.
#33. In 2021, more than 204000 people faced malicious login attempts to gain access to their banking details.
In 2020, nearly 90 percent of financial institutions dealt with ransomware cyber attacks.
#35. More than 100 financial bodies have been targeted by LokiBot.
As per ransomware statistics in 2021, LokiBot has extorted more than $2 million in revenue from these institutions.
#36. Banks saw a 520 percent boost in ransomware attempts and phishing from March to June 2020.
Experts say that there is an increasing threat to small financial facilities with a loss of $35 million in revenue.
#37. Kryptik Trojan malware was responsible for the most cyber attacks against financial institutions in 2020.
As per ransomware stats 2020, Kryptik Trojan malware accounted for 70 percent of 52 percent of cyber attacks carried out on financial institutions.
#38. Around 246 ransomware attacks have taken place against the US government organization in the last three years.
The US government has suffered a loss of $52.8 billion in ransom.
#39. As of 2020 stats, only 38 percent of local and state government workers are qualified in ransomware attack prevention.
#40. A ransomware cyber attack against New Orleans resulted in a loss of more than $7 million in revenue.
Ransomware Cryptocurrency Statistics
#41. As per ransomware statistics 2021, hackers earned more than $90 million in Bitcoins by launching a cyber attack on an oil company.
#42. In June 2020, a West Coast University gave away $1.14 million in Bitcoins to cyber criminals after a malware attack.
#43. Illegal activities contributed to 2.1 percent of all cryptocurrency transaction volume.
#44. In 2020, 7 percent of all funds of ransomware payments were received by cryptocurrency addresses.
#45. Colonial Pipeline has given $4.4 million in Bitcoins to cyber criminals after being hit by a ransomware attack.
Mobile Ransomware Trends
#46. As per ransomware statistics for 2020, nearly 4.2 million people in the US faced ransomware cyber hits on their mobile devices.
#47. There are more than 4,000 mobile threat variants have been found on the McAfee sample database.
#48. Ransomware stats in 2020 show that 900000 Android phones were attacked by ScarePakage ransomware in just 30 days.
#49. Over 68000 new ransomware Trojans were identified for mobile in 2019.
Expenses Of Ransomware Cyber Attacks
#50. The worth of ransom demands has shot up in recent years.
The ransomware statistics in 2021 reveal that some ransom demands have shot up to $1 million in the past few years.
#51. The average cost of recuperating from a cyber hit is $1.85 million.
#52. The average payout by mid-sized trades has been $170404.
#53. Average downtime of 22 business days caused by ransomware attacks costs a loss of over $8500 per hour to firms.
Ransomware Projection Statistics
#54. Many countries are supposed to collaborate extensively to extradite and prosecute cyber criminals in 2022.
#55. Ransomware is going to be the most popular trick used in software to carry out attacks against supply chain and third-party data violations.
#56. Remote employees are the major targets of cyber attacks.
#57. 60 percent of entrepreneurs, firms, and investors will treat cybersecurity risk as the key factor in assessing new business prospects by 2025.
#58. 30 percent of firms will opt for zero trust network access (ZTNA) models by 2024.
Various Evolving Ransomware Variants
#59. Netwalker is a ransomware strain that has been designed by a cybercrime group called Circus Spider.
This strain of ransomware helps hackers gain access to malware code in exchange for a fraction of the funds.
#60. Darkside is the new strain of ransomware.
It carries out theft, backup, and encryption of confidential data.
#61. Conti is one of the most dangerous strains of ransomware.
It utilizes a double-extortion method to encrypt an infected system. Hackers from this group usually send phishing emails to users that originate from a trustworthy address.
#62. REvil has been able to extort a large sum of money from its victims.
It is also called Sodin and Sodinokibi. It encourages underground cybercrime forums as well.
Methods To Prevent Ransomware Attacks
#63. Using cyber security training within the firm will help employees understand the value of cyber security.
Implementing such training will help improve work culture as well.
#64. Users should refrain from clicking on suspicious links.
Users need to be aware of opening or clicking on unsolicited documents, emails, or links. As per Data Breach Investigations Report 2021, phishing has led to 70 percent of data breaches.
#65. Users should maintain offsite backups.
It is essential to back up confidential data. During a ransomware incident, users should limit access to backups as cyber criminals often attack backup files to reduce users' ability to restore their data.
#66. Use a strong password system.
Users or firms should use a two-factor authentication system to prevent password sharing and overdoing of the same password. Using an SSO system for additional password security might be a beneficial choice.
#67. It is advisable to use email and endpoint protection.
Users should carefully scan all emails, links, and malicious documents and keep updating firewalls and endpoint detection software with the latest malware signatures.
Reducing The Effect of Ransomware Attack
#68. Use a Zero-Trust Network Access Model (ZINTA).
ZINTA needs you to verify all users and devices that connect to the network each time they try to log in. Monitoring the activity on the server is also very crucial to make sure that users gain access to only what they require.

(Source: Zindagitech.com)
#69. Using User and Entity Behavior Analysis tools (UEBA) might be beneficial.
It is vital to keep a close watch on signs that indicate ransomware activities. UEBA tools send alerts if users or devices start behaving oddly and execute automatic retorts to stop threats in their tracks.
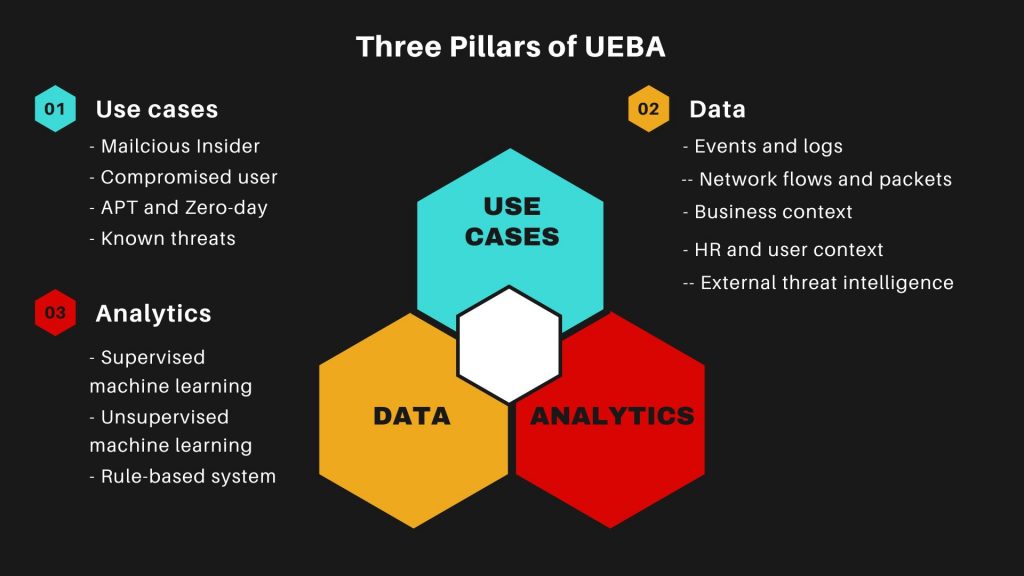
(Source: Imperva)
#70. Reducing the blast radius can be helpful.
The blast radius is the amount of damage caused by a single compromised random user or device. One should immediately limit access to sensitive data to lessen the blast radius.
Conclusion
These ransomware statistics indicate that no one is spared from the danger of such cyber attacks. The number of individuals, organizations, and investors who are affected by cyber-attacks is growing day by day. The data shows that many businesses are planning to spend exorbitant amounts of money on preventing ransomware cyber attacks and mitigating their impact. It is evident how essential it is to implement a protection system to secure sensitive data and networks. Although cybercrime is not going away any time soon, it is vital to stay ahead of such cybercriminals.
Sources
FAQ.
As per the ransomware statistics of the first quarter of 2021, the median length of disruption after ransomware cyber hit on businesses in the US has been 22 days.
As per a survey, nearly 37 percent of organizations have been affected by ransomware attacks in 2021.
The average ransomware payout has shot up by 82 percent in 2020 to a record $570000 in the first quarter of 2021.
The average ransom for small trades is about $5900.
Ransomware often attacks by sending phishing emails, links, or malicious attachments. It also attacks via drive-by downloading.

Barry is a lover of everything technology. Figuring out how the software works and creating content to shed more light on the value it offers users is his favorite pastime. When not evaluating apps or programs, he's busy trying out new healthy recipes, doing yoga, meditating, or taking nature walks with his little one.